Apr 27, 2009 Little Snitch is an outgoing firewall, and is a very very good app to have. It is very useful at stopping trojans from sending out your data, stopping apps from 'phoning home', and your application serial number and registration from being sent out, should you wish to prevent it. Traceroute fails ('No route to host'). I traveled back home and the it persists in my home network but it is not as intense as before (i.e. Some of the websites, like Facebook, seem to work ok, others still nothing).
Download FREE Little Snitch v4.5 Multilingual Full Crack for Mac!
Little Snitch gives you control over your private outgoing data.
Track background activity
As soon as your computer connects to the Internet, applications often have permission to send any information wherever they need to. Little Snitch takes note of this activity and allows you to decide for yourself what happens with this data.
Control your network
Choose to allow or deny connections, or define a rule how to handle similar, future connection attempts. Little Snitch runs inconspicuously in the background and it can even detect network-related activity of viruses, trojans, and other malware.
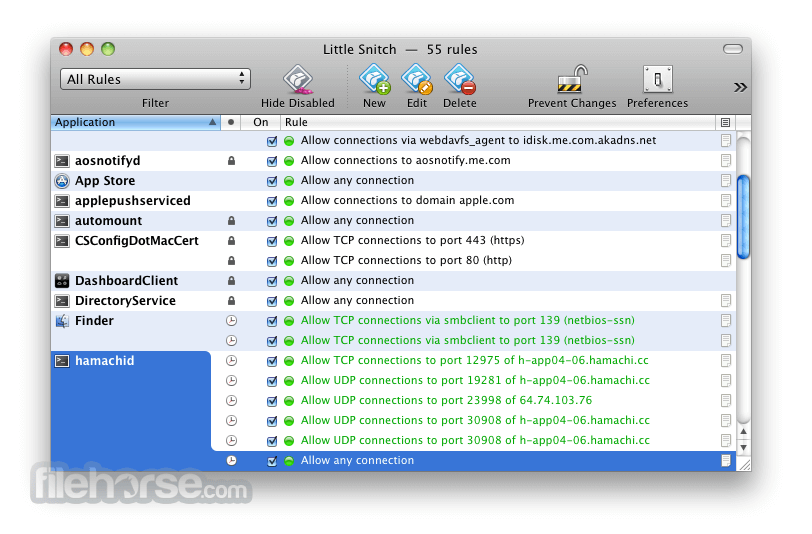
Little Snitch For Pc
Filter connections and monitor your network traffic with ease
The Little Snitch Network Monitor utility features a well-designed interface and provide easy-to-read animated and informative diagrams created based on real time traffic information. Hence, you can analyze bandwidth, connectivity status, traffic totals, detailed traffic history for the past hour and more.
You can filter the displayed data based on the process name or server port and group them according to your needs. Little Snitch helps you view traffic peaks, check the average bandwidth and save snapshots for further analysis.
Enable the Silent Mode for a distraction free working environment
The network traffic can be easily captured in the PCAP format while the network activity is displayed along various system events in order to provide a context. There is also a Silent Mode that allows you to get on with your work without being interrupted by any network related notifications. However, you can review the Silent Mode Log to create rules for connection attempts that took place during this period.
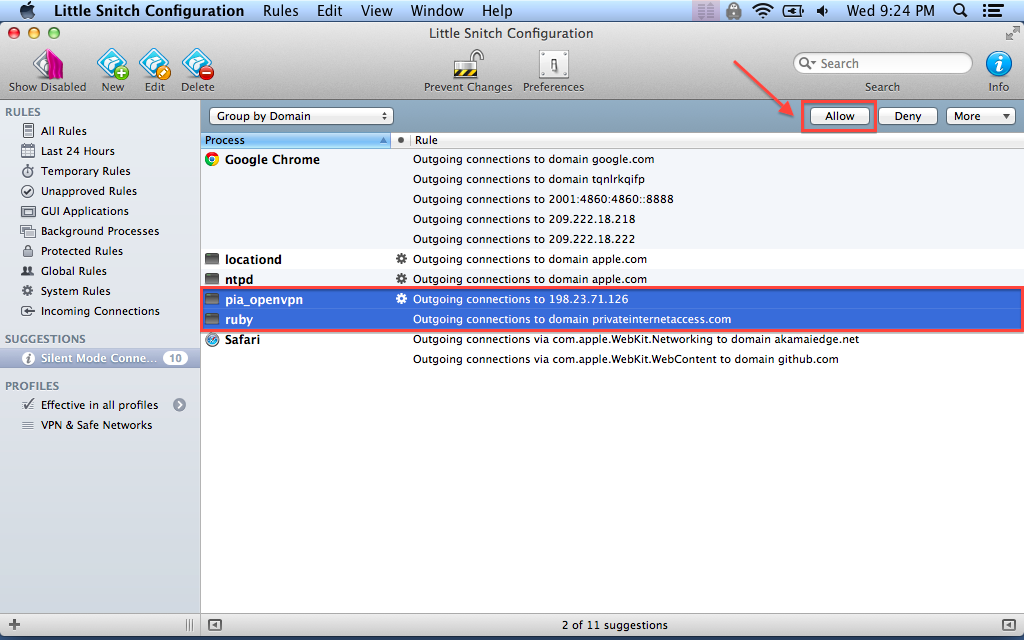
On top of that, you can group your rules in different profiles and enable them only when a particular profile is active. Thanks to Little Snitch’s status bar menu, you can choose the desired profile with just a few mouse clicks.
Enjoy the versatility of the Automatic Profile Switching function
At the same time, you can take advantage of the Automatic Profile Switching feature and associate different networks with certain profiles. Once the network is detected, the associate profile is automatically enabled. For example, you can use a set of filters when you are at home and more restrictive ruleset when you access the web from an Internet Cafe.
What is more, Little Snitch features a flexible temporary rule system that offers a number of options for rules that are effective only for a limited period of time. Furthermore, Little Snitch automatically analyzes your ruleset and indicates the presence of overlapping, redundant or invalid rules that you might want to delete.
- Intel 64
- OS X 10.11.0 or later
Can't Access Little Snitch Site Full
Home Page: https://www.obdev.at/products/littlesnitch/index.html
- CAN NOT DOWNLOAD: Some probably encounter the following error: This site can’t be reached ...sundryfiles.com’s server IP address could not be found. DNS_PROBE_FINISHED_NXDOMAIN. In this case, please use Google DNS and you will get rid of trouble.
- If downloaded file can not be extracted (file corrupted...), please make sure you have downloaded the file completely and don't use Winzip, it sucks! We would recommend using The Unarchiver.
- By reason, the App does not work and can not be opened. Mostly, just Disable the Gatekeeper, and you get rid of troubles.
Little Snitch Crack
As Tinkster pointed out the first step is to take the machine off line. It is best to do this by either disconnecting the network cable or putting up a firewall (iptables) to only allow SSH connections from a trusted source. Once you have secured the machine you can work with much less possibility of interference. The next step would be to review the CERT intruder detection checklist. It will give you an overview of the investigation process. Don't worry if a lot of it doesn't make sense, we can help with that.
Now, to begin, would you please describe what is happening that leads you to suspect that your machine may have been compromised? Please provide as much specific detail as possible, including log entries if you have them.



